When to Use PAT vs OAuth: For most users, we recommend using Snowflake OAuth as the preferred authentication method. PAT is an alternative for users who cannot set up OAuth integrations or need a simpler authentication approach.
What This Guide Covers
This documentation will help you:- Understand when PAT is appropriate - Learn when to use PAT vs OAuth
- Generate a Snowflake PAT - Create a programmatic access token in Snowflake
- Configure Gumloop - Add your PAT credentials to connect Gumloop to Snowflake
- Handle Network Policies - Understand and configure network policy requirements
OAuth vs PAT: Which Should You Use?
Use OAuth (Recommended)
- Enhanced security with temporary tokens
- Automatic token refresh
- Centralized access control
- Better audit trail
- Set up OAuth →
Use PAT When
- OAuth integration setup is not feasible
- You need a simpler authentication method
- Your organization restricts OAuth integrations
- You need quick access for testing
Prerequisites
Before you begin, ensure you have:- Snowflake Account Access - A Snowflake user account with permissions to generate PATs
- Account Identifier - Your Snowflake account identifier (e.g.,
myorg-account123) - Network Policy Considerations - Understanding of your organization’s network policies (see Network Policy Requirements below)
Step 1: Generate a Snowflake PAT
1.1 Access the PAT Settings
- Log in to your Snowflake account
- Click on your profile icon in the bottom-left corner
- Select My Profile
- Navigate to the Authentication section
- Find Programmatic access tokens
1.2 Generate a New Token
- Click Generate new token
- Enter a descriptive name for the token (e.g., “Gumloop”)
- Set an appropriate expiration date
- Click Generate
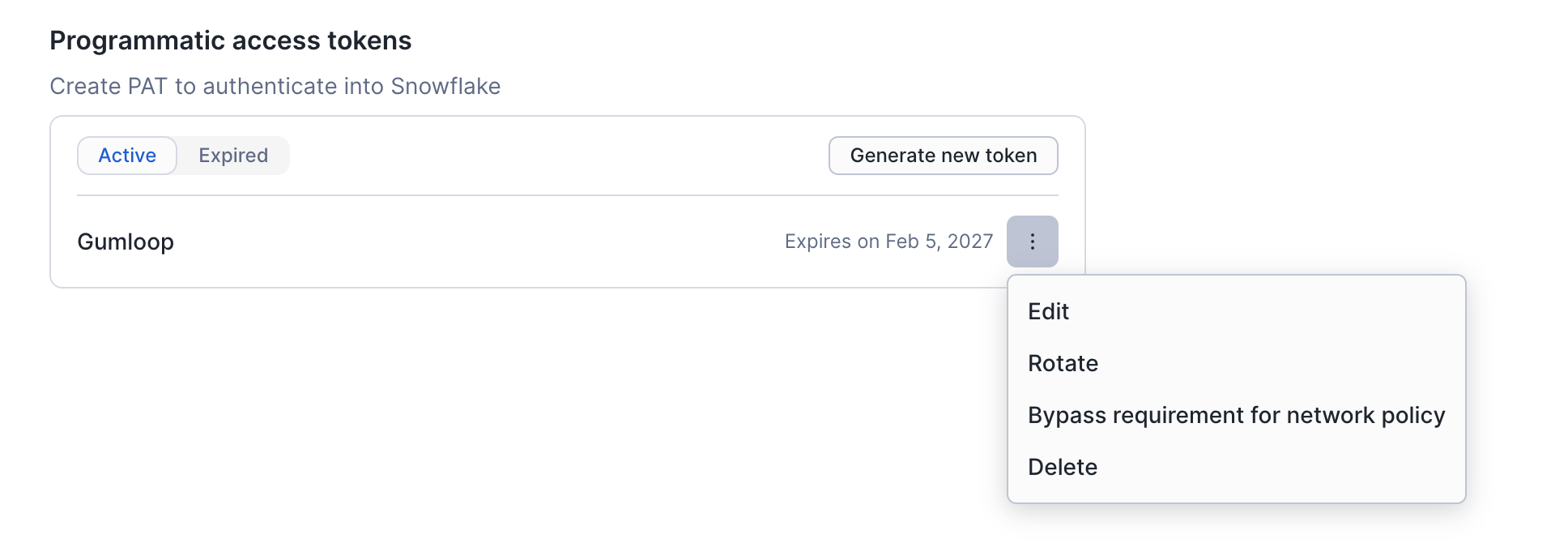
1.3 Token Management Options
After creating your token, you can manage it through the menu (three dots):- Edit - Modify token settings
- Rotate - Generate a new token value while keeping the same configuration
- Bypass requirement for network policy - Temporarily bypass network restrictions (see below)
- Delete - Remove the token
Step 2: Configure Gumloop
2.1 Add Snowflake PAT Credentials
- Navigate to Gumloop Personal Credentials Page
- Click Add Credential
- Search for “Snowflake PAT” in the Snowflake PAT tab
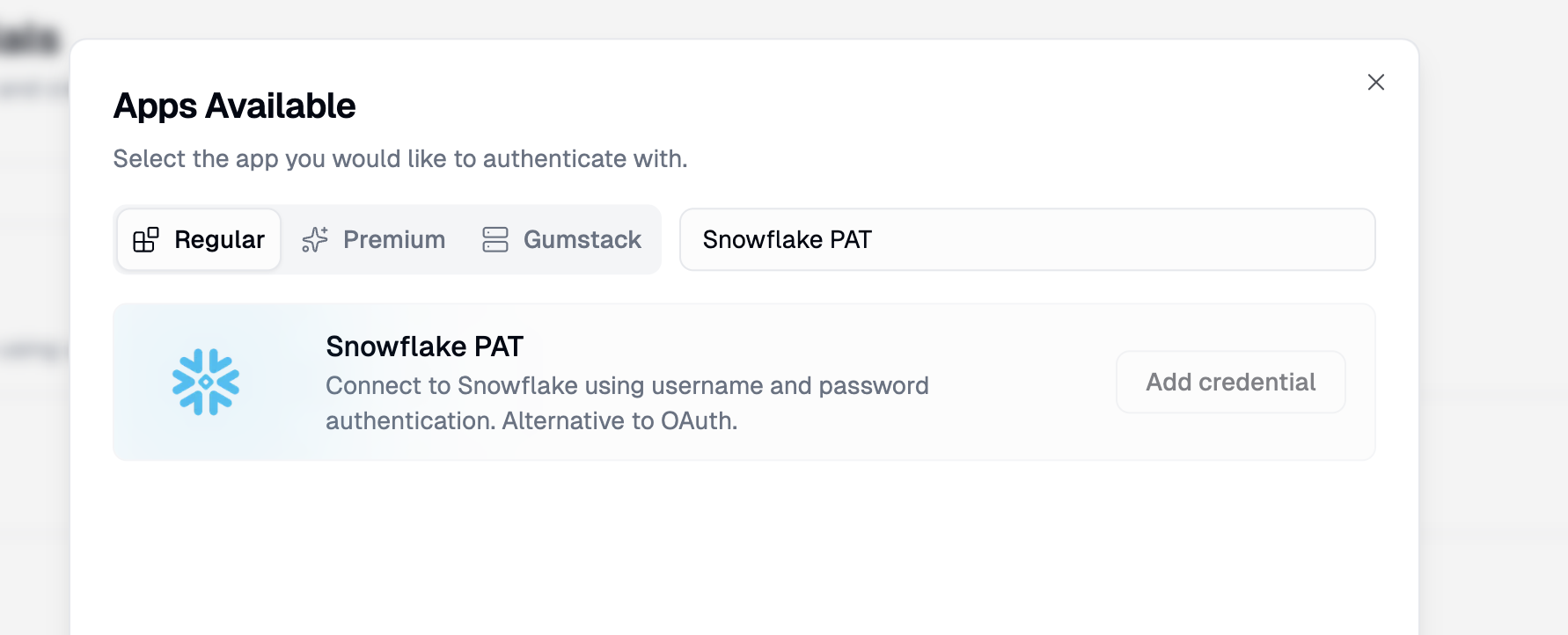
- Click Add credential on the Snowflake PAT option
-
Enter the following information:
- Username: Your Snowflake username
- Password: The PAT token you generated in Step 1
- Account Identifier: Your Snowflake account identifier (e.g.,
myorg-account123)
- Click Save to store your credentials
2.2 Verify Your Connection
To confirm your PAT connection is working:- Create a new agent or workflow with a Snowflake Reader node or the Snowflake MCP integration
- Configure a simple query like
SELECT CURRENT_USER() - Run the agent or workflow to verify the connection succeeds
Network Policy Requirements
Snowflake network policies can restrict which IP addresses are allowed to connect. When using PAT authentication, you may encounter network policy restrictions that block connections from Gumloop’s servers.Understanding Network Policies
Network policies in Snowflake control access based on IP addresses. If your organization has network policies configured, PAT connections from Gumloop may be blocked unless:- Gumloop’s IP range is whitelisted in your network policy, OR
- You temporarily bypass the network policy requirement for your PAT
Option 1: Whitelist Gumloop’s IP Range (Recommended for Production)
For production use, contact your Snowflake administrator and reach out to Gumloop to add Gumloop’s IP range to your network policy’s allowed list. This provides permanent access without requiring repeated bypasses.Option 2: Temporary Network Policy Bypass (For Testing)
For testing purposes, you can temporarily bypass the network policy requirement:- Go to your Snowflake profile → Authentication → Programmatic access tokens
- Click the menu (three dots) next to your token
- Select Bypass requirement for network policy
- Set the bypass duration (maximum 24 hours)
When Network Policy Bypass is Needed
You may need to bypass or whitelist if:- Your Snowflake account has network policies restricting access to specific IP ranges
- You receive connection errors mentioning “network policy” or “IP not allowed”
- PAT authentication fails even with correct credentials
Troubleshooting
Connection Refused or Network Policy Error
Problem: Getting a network policy error when connecting Solution:- Use the temporary bypass option for testing (see Option 2 above)
- For production, whitelist Gumloop’s IP range in your Snowflake network policy
Invalid Credentials Error
Problem: Authentication fails with invalid credentials Solution:- Verify your username is correct
- Ensure you’re using the PAT token (not your regular password) in the Password field
- Check that the Account Identifier matches your Snowflake account URL
- Confirm the PAT hasn’t expired
Token Expired
Problem: Previously working connection now fails Solution:- Check if your PAT has expired in Snowflake
- Generate a new token and update your Gumloop credentials
- Consider setting a longer expiration when creating new tokens
Warehouse Access Issues
Problem: Connected but queries fail with warehouse errors Solution:- Ensure your user has USAGE privilege on the warehouse
- Specify the warehouse explicitly in the Snowflake Reader node
- Check if a default warehouse is configured for your user
Security Best Practices
Token Expiration
Set appropriate expiration dates for your PATs. Shorter durations are more secure but require more frequent rotation.
Least Privilege
Use a Snowflake user with only the minimum permissions needed for your workflows.
Regular Rotation
Periodically rotate your PAT tokens to maintain security, even before they expire.
Secure Storage
Never share PAT tokens in plain text. Gumloop encrypts your credentials securely.
Additional Resources
- Snowflake OAuth Configuration - Recommended authentication method
- Snowflake Programmatic Access Tokens Documentation
- Snowflake Network Policies
- Gumloop Credentials Guide
Need Help?
If you encounter issues not covered in this guide:- Check the Snowflake PAT documentation for detailed technical information
- Contact your Snowflake administrator for account-specific issues
- Reach out to Gumloop Support for integration assistance

