What Are Custom User Roles?
The Custom User Roles system is built around a flexible group-based architecture with automatic default role assignment. Every organization member is assigned to a role that determines their permissions across the platform—from basic feature access to specific integration scopes and AI model usage.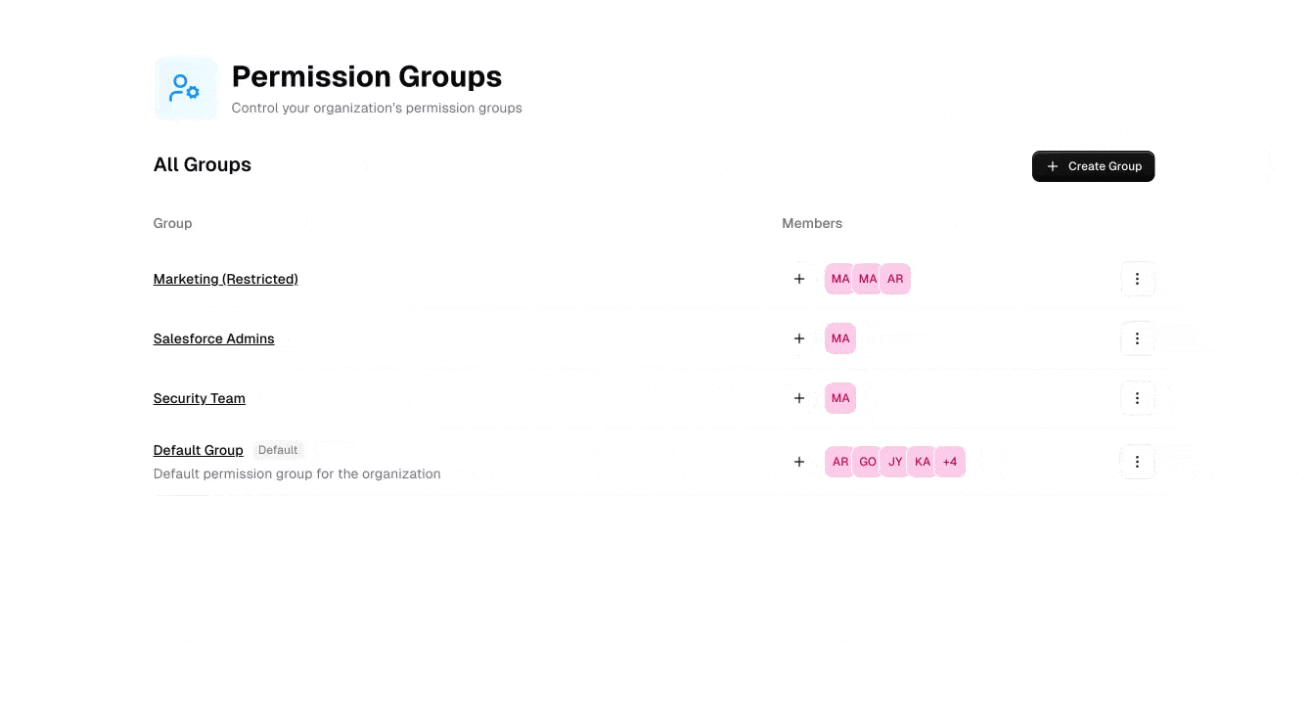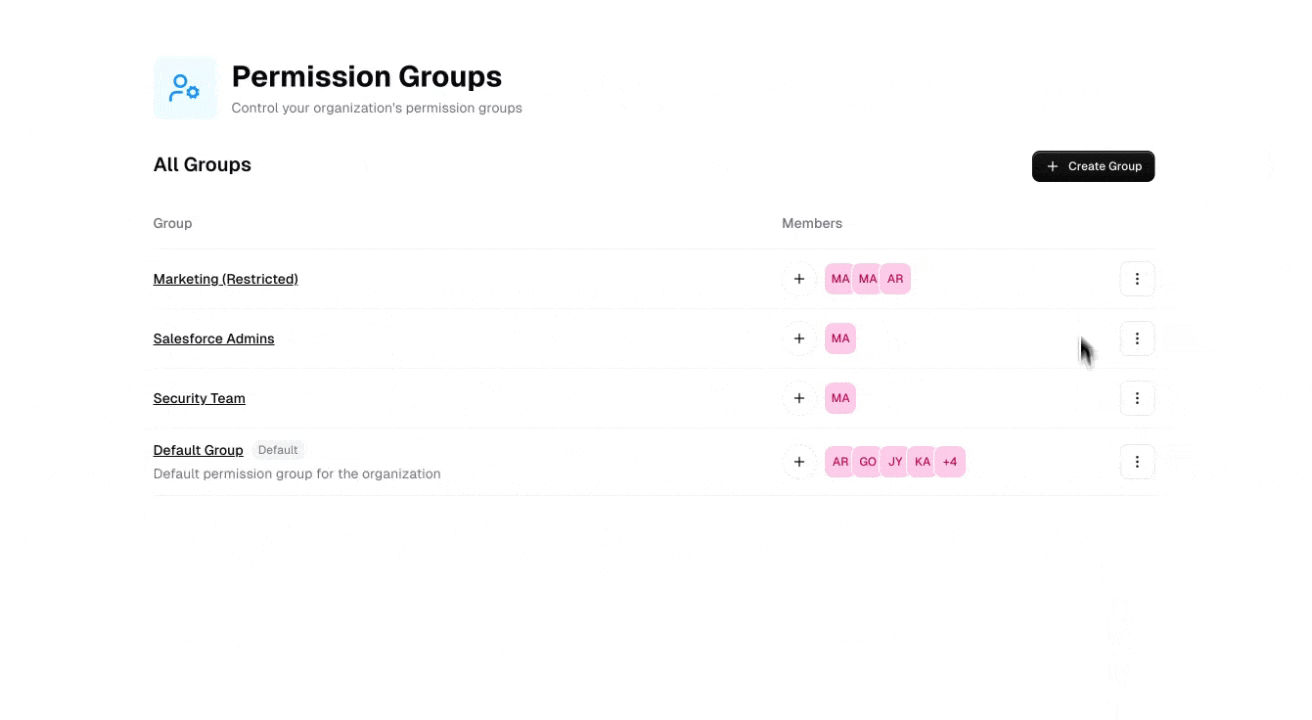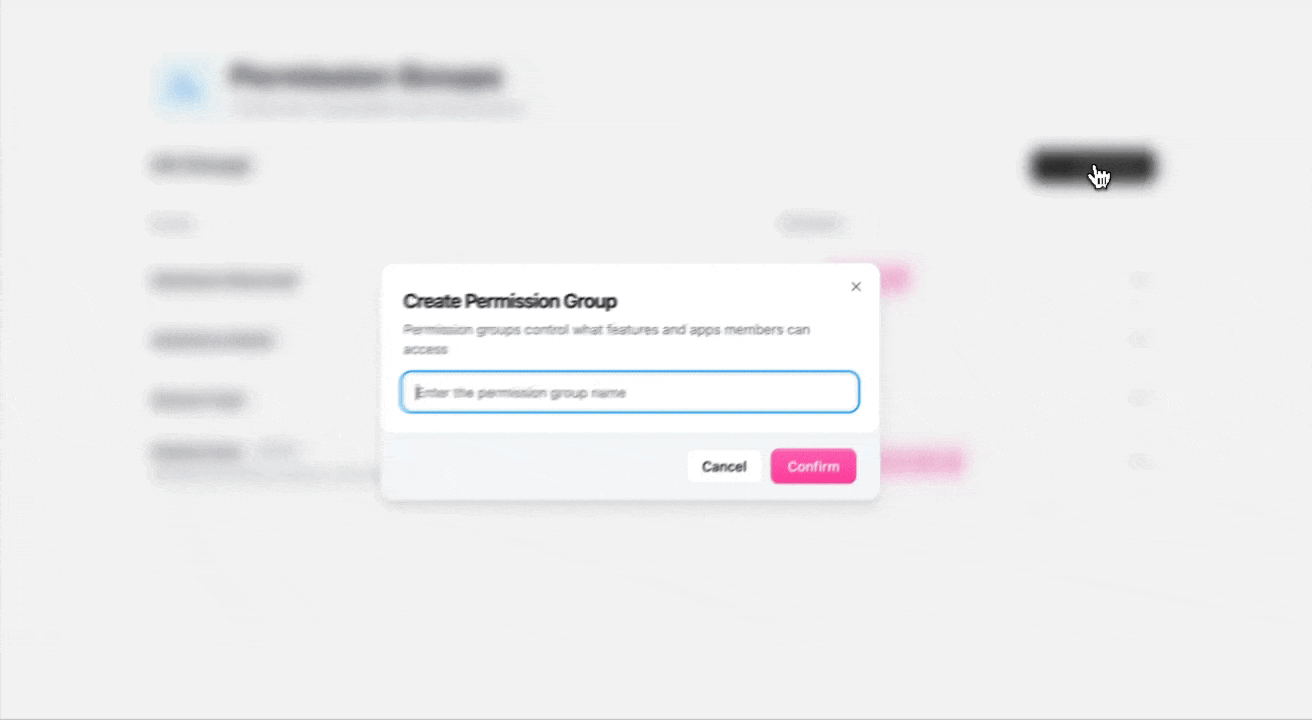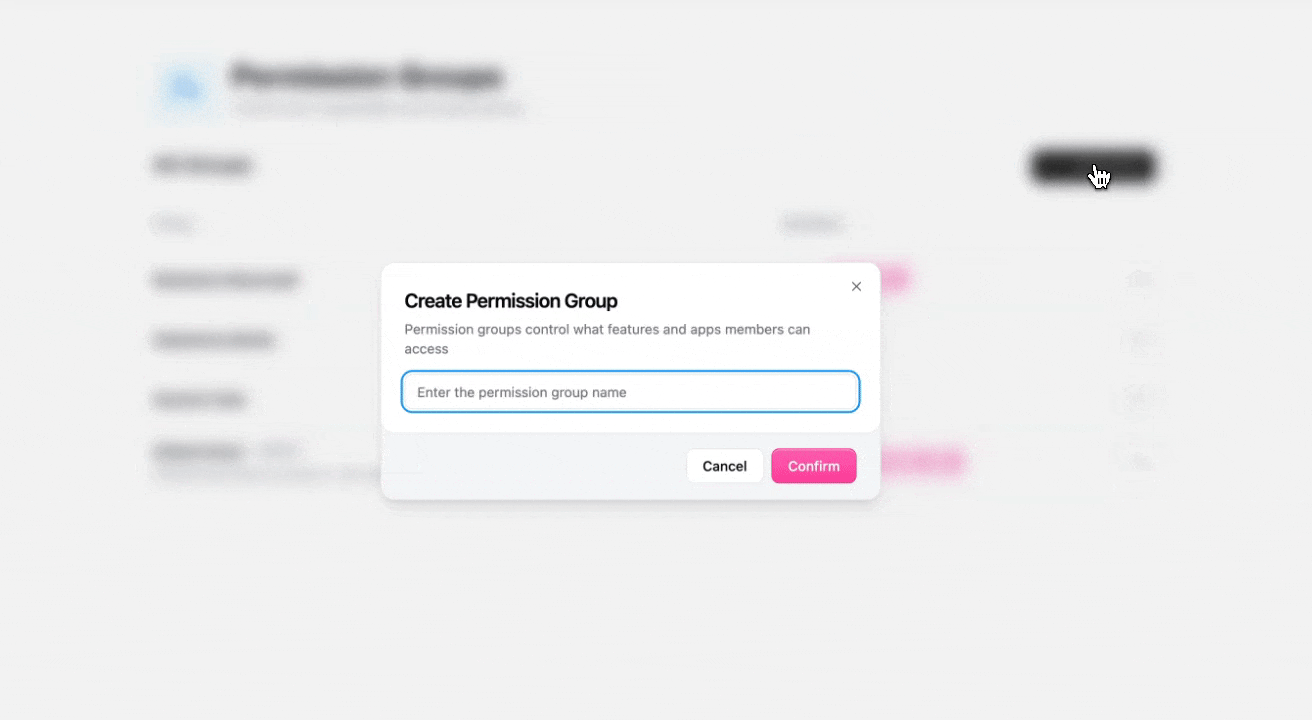
Role-Based Access
Control what users can do based on their responsibilities
Automatic Assignment
New members automatically join the default role
Enterprise Security
Maintain compliance with granular permission controls
Default Role System
Every organization starts with a default role that provides baseline permissions for all members.- How It Works
- Key Properties
When an organization is created, Gumloop automatically:
- Creates a Default Role: Named “Default Group” with baseline permissions for all organization members
- Auto-assigns New Members: All users joining the organization are automatically added to the default role
- Provides Fallback Protection: Users removed from other roles automatically return to the default role
The default role ensures no user is ever left without access permissions. Even if removed from all custom roles, users maintain their baseline access through the default role.
Managing User Roles
Accessing Role Management
Navigate to your organization’s role settings at: gumloop.com/settings/organization/roles-permissions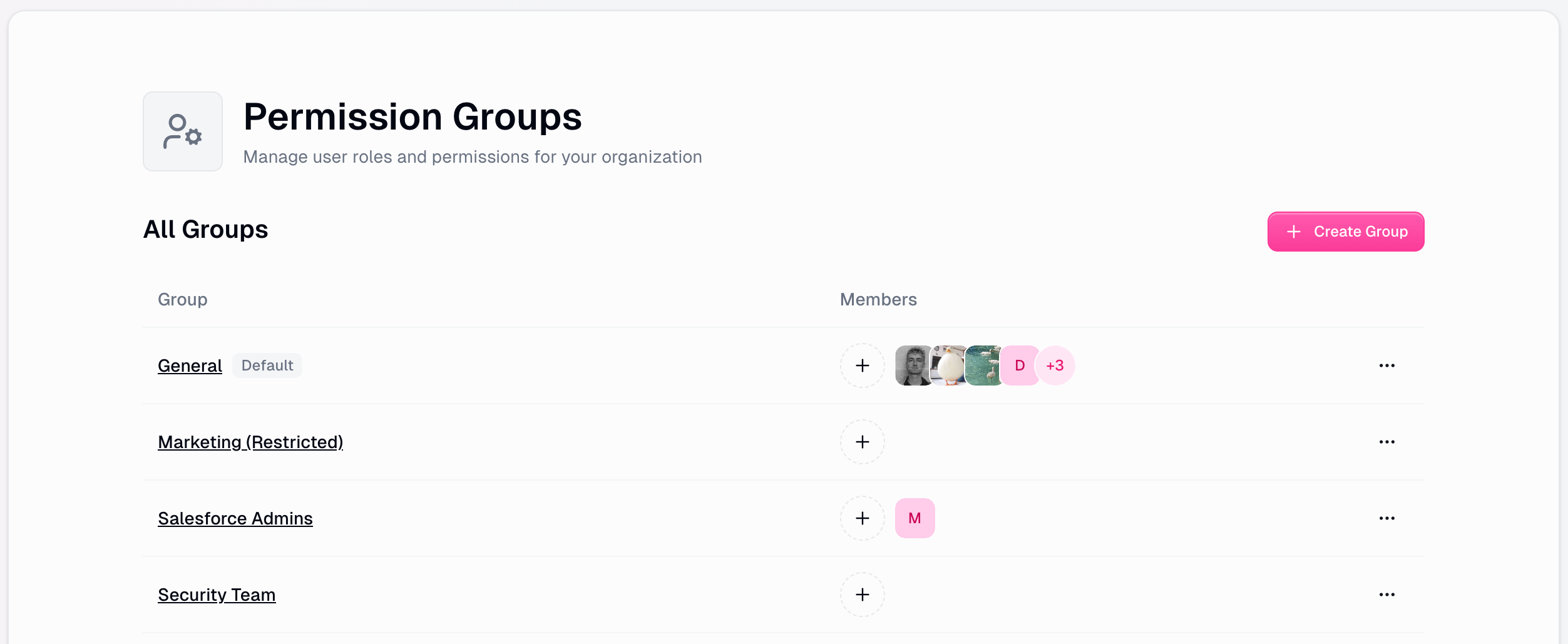
Creating Custom Roles
Provide Group Details
Enter a descriptive group name and description that reflects the role’s purpose
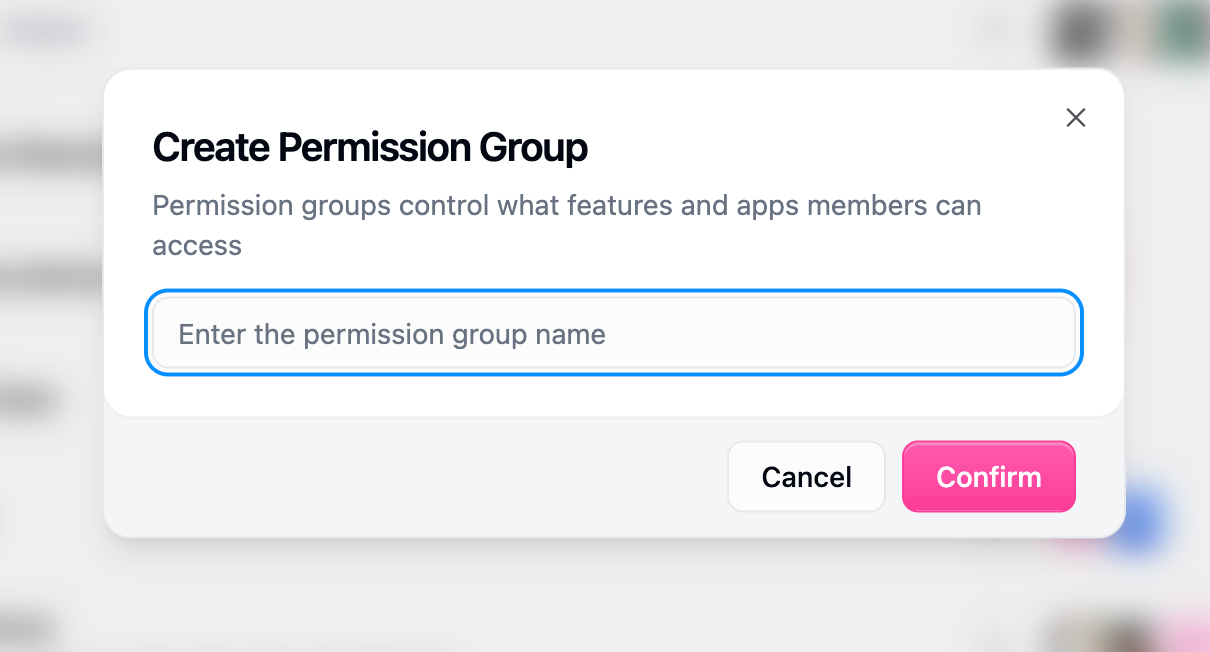
Role Management Actions
Rename
Update group names and descriptions to match your organization’s structure
Set as Default
Designate which group new members receive automatically
Delete
Remove custom groups (default roles cannot be deleted)
View Members
See how many users are assigned to each group

Permission Categories
1. Members Management
Control which users belong to each role with search, add, and remove capabilities.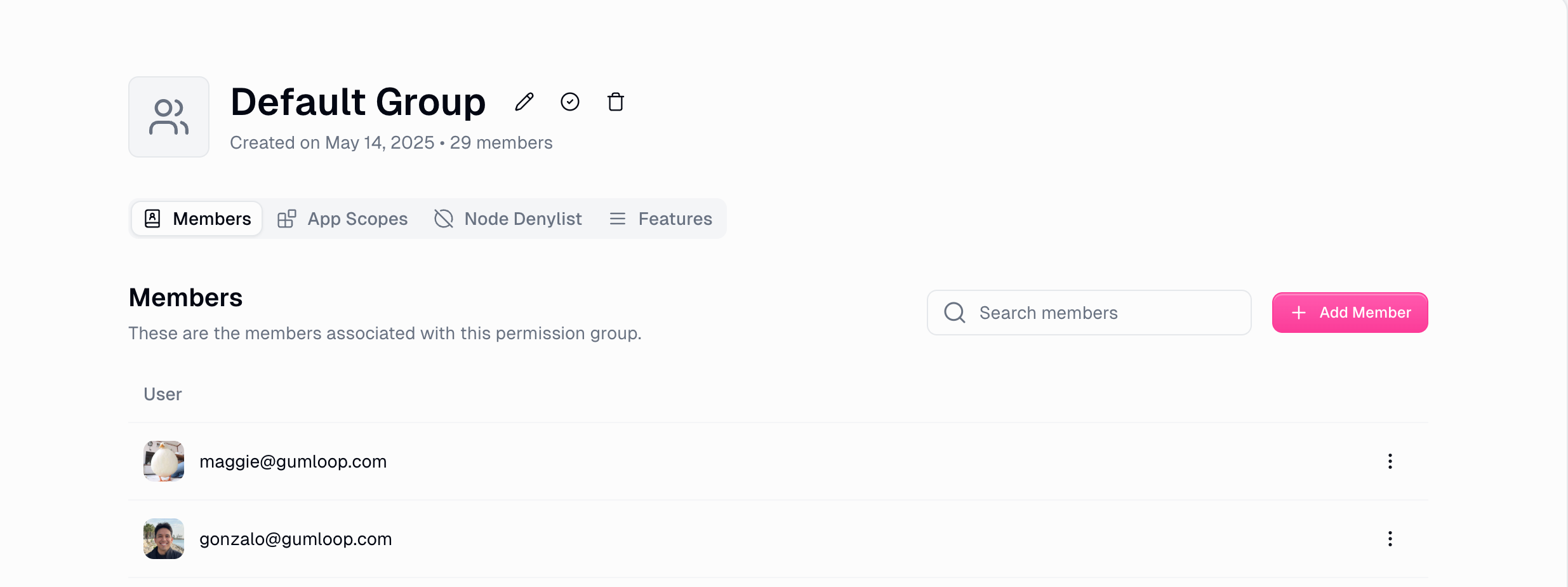
Search & Add
Find users by email with real-time search and add them to roles with a single click
Important Rules
- Users can only belong to one group at a time
- Moving users automatically removes them from previous groups
- Users can’t be removed from default group without reassignment
2. Features Restrictions
Control access to core Gumloop platform features with granular toggle controls.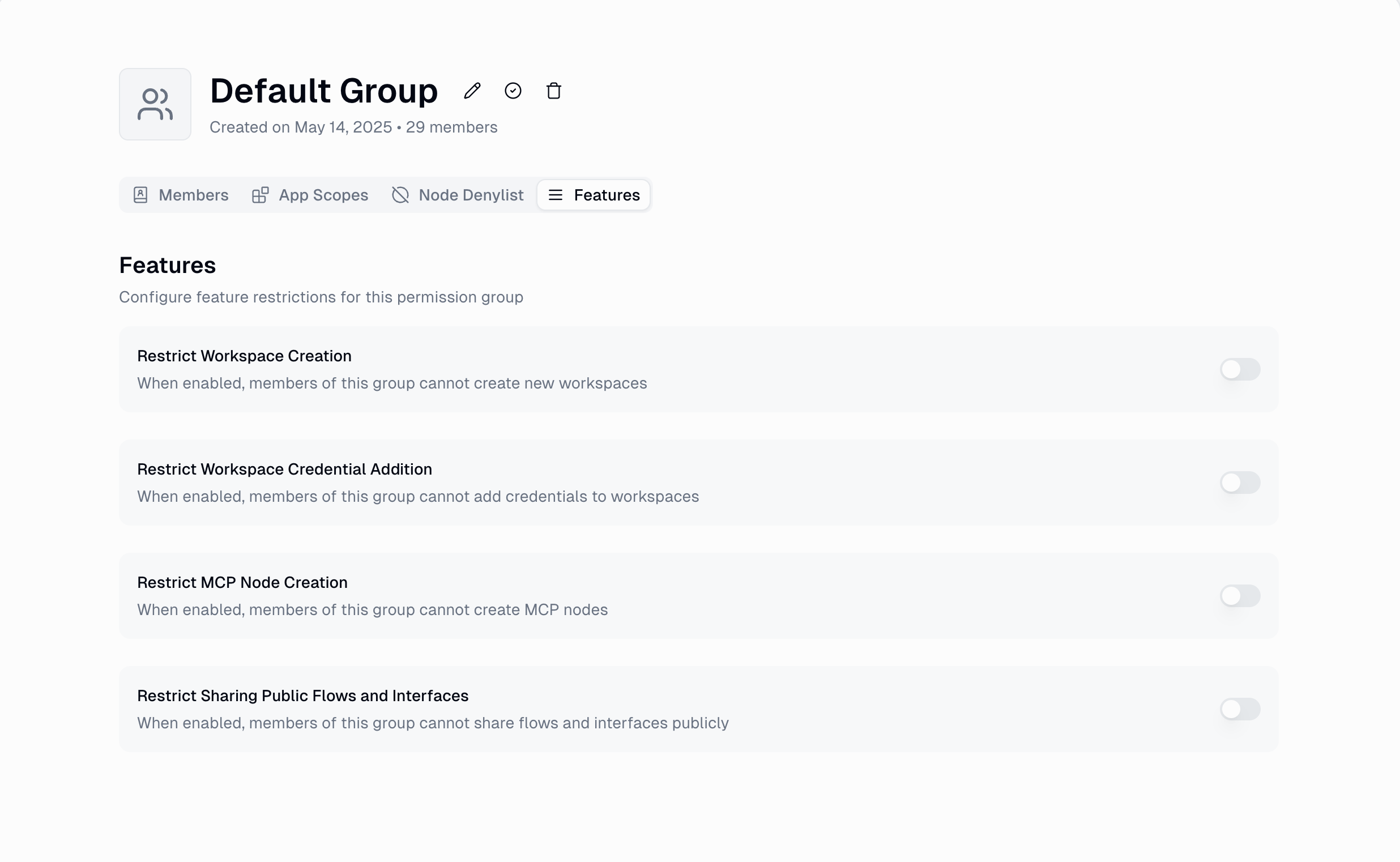
Available Feature Restrictions
| Feature | Description | Impact |
|---|---|---|
| Workspace Creation | Prevents users from creating new workspaces | Users can only join existing workspaces they’re invited to |
| Workspace Credential Adding | Blocks adding new credentials to workspaces | Users can only use personal credentials or existing workspace credentials |
| MCP Node Creation | Restricts creation of custom MCP nodes | Users cannot build custom MCP nodes |
| Public Sharing | Prevents sharing workflows and interfaces publicly | Users can only share within the organization |
Feature restrictions use simple toggle switches with real-time updates and immediate effect—no saving or deployment required.
User-Based Rate Limits
User-Based Rate Limits allow organization administrators to set custom concurrent workflow execution limits for specific user groups. This is particularly useful for managing compute resources across different user types.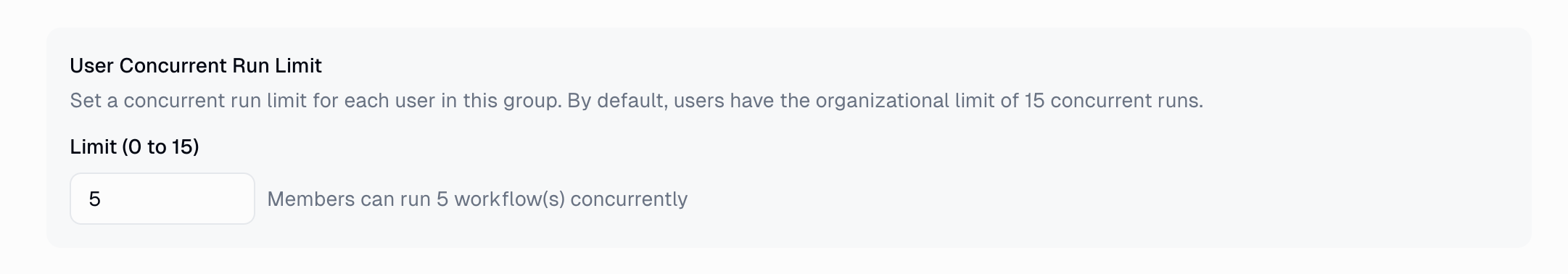
- What Are Concurrent Runs?
- How It Works
- When to Use
A concurrent run represents a separate workflow execution happening at any given moment. This is distinct from:
- Subflow executions: Nested workflows within a parent workflow
- Loop mode iterations: Multiple items being processed within a single workflow run
- Individual node executions: Steps within a workflow
Navigate to Role Settings
Select or Create Permission Group
Create a new permission group or select an existing one to configure
Configure Rate Limit
Go to the Features tab, locate “User Concurrent Run Limit”, and set the appropriate limit
Understanding Concurrent Run Scale
| Concurrent Runs | Usage Pattern | Example Use Cases |
|---|---|---|
| 1-3 runs | Light users | Occasional workflow testing, infrequent automation needs |
| 3-8 runs | Regular users | Daily automation tasks, moderate workflow usage |
| 8-12 runs | Power users | Frequent automation specialists, team workflow managers |
| 12-15 runs | Heavy automation | Dedicated automation teams, mission-critical business processes |
Best Practices
Start Conservative
Begin with the default organization limit for most users. Create specialized groups only for proven high-volume needs.
Monitor and Adjust
Review concurrent run usage regularly. Adjust limits based on actual usage patterns rather than anticipated needs.
Communicate Limits
Inform users of their concurrent run limits and provide guidance on optimizing workflows to respect capacity constraints.
3. App Scopes (OAuth Permission Control)
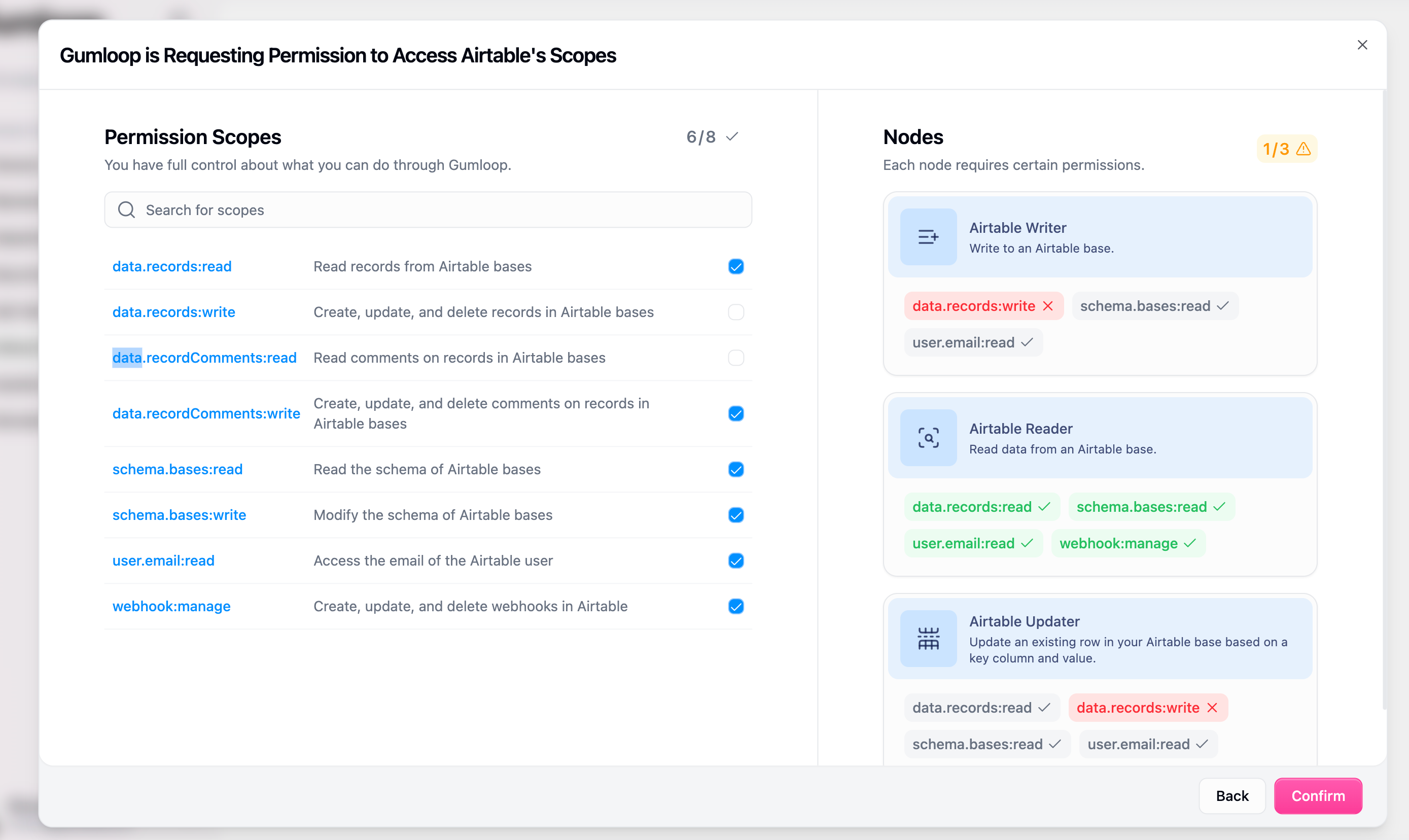
Manage which OAuth scopes users can access for third-party integrations with category-based control.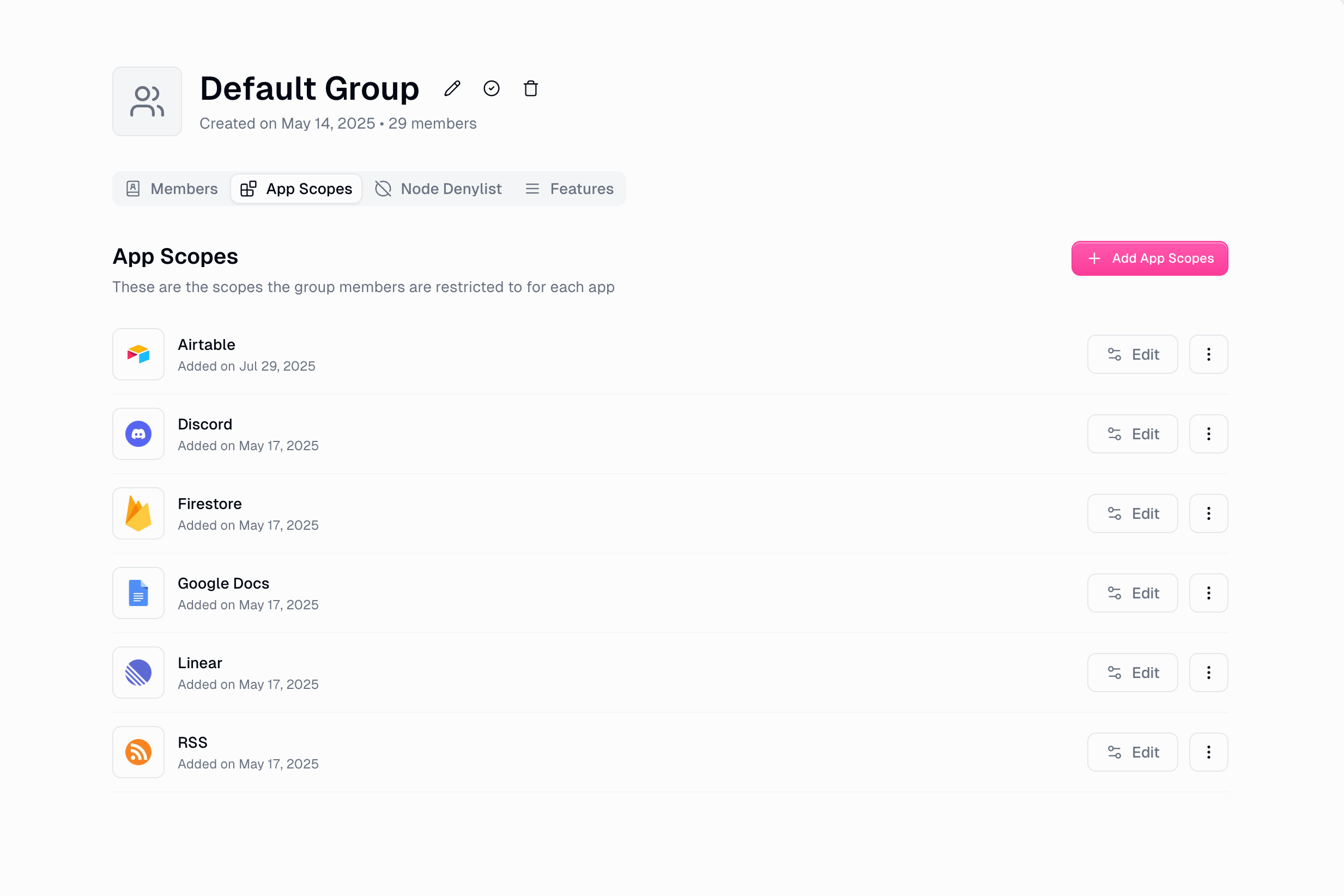
- How App Scopes Work
- Example Use Cases
- Configuration Steps
- Control permissions for each integration category (Google, Slack, Notion, etc.)
- Restrict specific OAuth scopes while allowing others
- Granular control over what data users can access in connected services
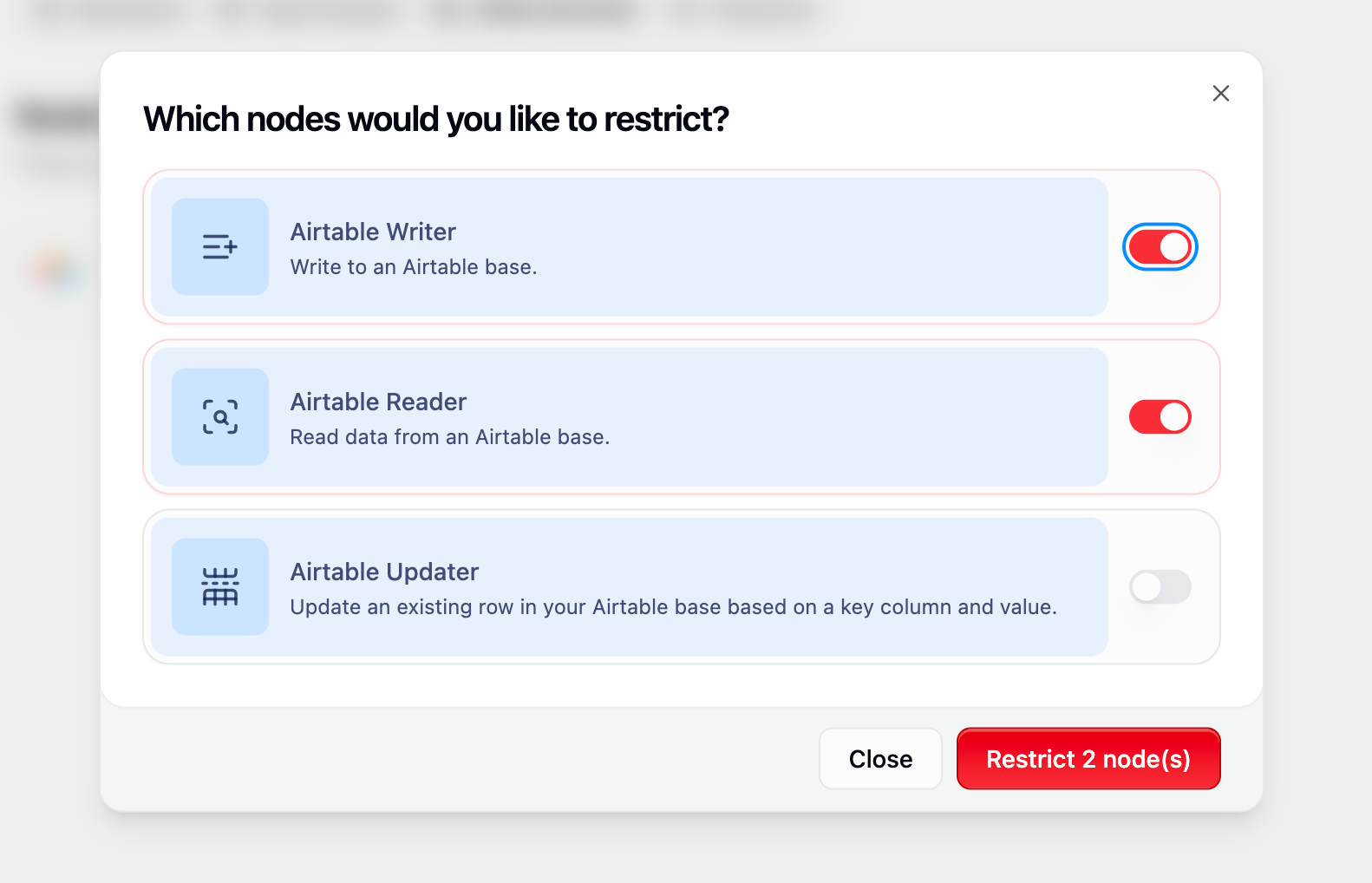
4. Node Denylist
Block access to specific workflow nodes and integrations to prevent unauthorized actions.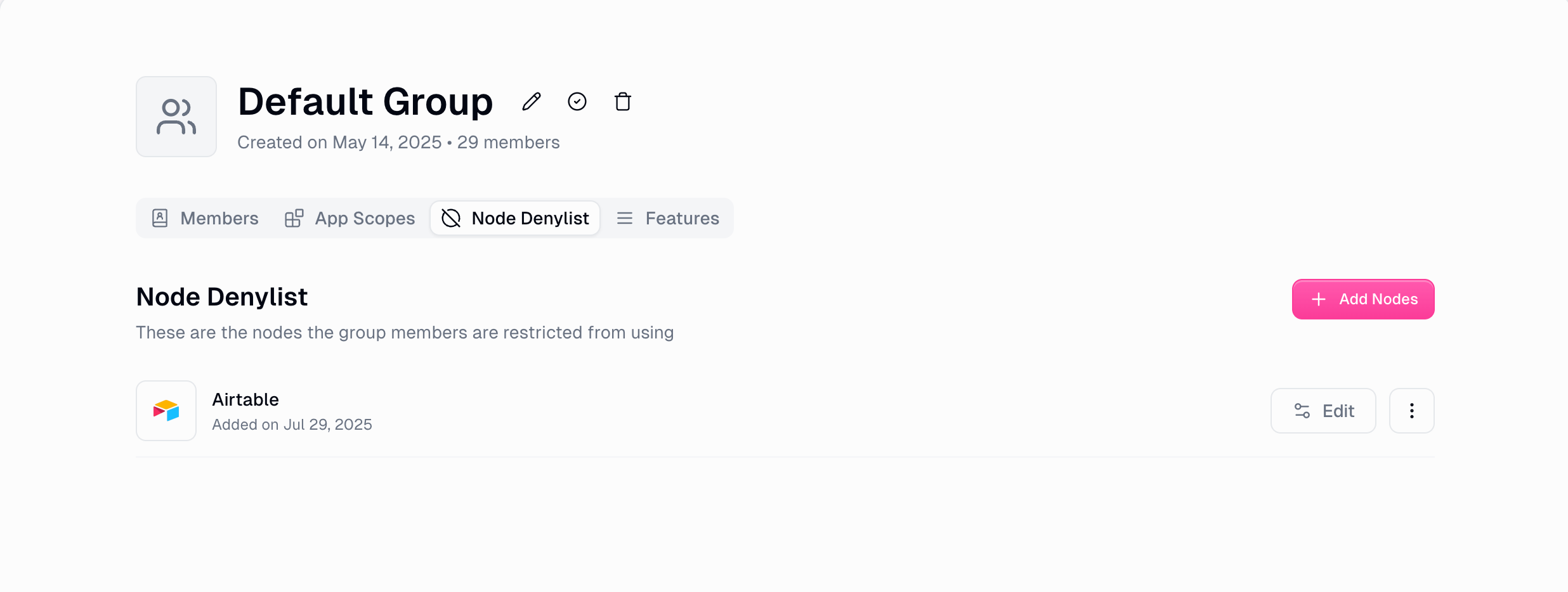
- Functionality
- Common Scenarios
- Implementation Details
- Category-based Restrictions: Block entire categories of nodes (e.g., all Salesforce nodes)
- Individual Node Control: Restrict specific nodes while allowing others in the same category
- Runtime Enforcement: Restrictions are enforced during workflow execution
Business Rules and Enforcement
Single Group Membership
Rule: Users can only belong to one group at a timeEnforcement: Adding a user to a new group automatically removes them from their previous groupBenefit: Prevents permission conflicts and simplifies access control
Runtime Permission Checks
When Applied: All permissions are checked in real-time during platform usageScope: Applies to UI interactions, workflow execution, and API callsResponse: Blocked actions show clear error messages explaining the restriction
Admin-Only Management
Access Control: Only organization administrators can manage user rolesPurpose: Ensures proper governance and security controls across the organization
Real-World Use Cases
Sales Team Access Control
Sales Team Access Control
Scenario: Your sales team needs CRM access but other teams shouldn’t view sensitive sales data.Solution:
- Create a “Sales” role with Salesforce integration access
- Grant OAuth scopes for lead reading and updating
- Restrict other departments from accessing Salesforce nodes
- Allow CRM data reading but prevent record deletion
IT and Operations Segregation
IT and Operations Segregation
Scenario: IT teams need full platform access while regular users need limited capabilities.Solution:
- Create an “IT Admins” role with full workspace creation rights
- Enable IT teams to manage workspace credentials
- Create an “Operations” role with advanced integrations
- Restrict marketing to basic tools in a separate role
Compliance and Security
Compliance and Security
Scenario: Your organization must comply with data handling regulations and prevent unauthorized sharing.Solution:
- Prevent certain teams from sharing workflows publicly
- Restrict access to financial integrations for non-finance users
- Block sensitive data writing nodes for audit teams
- Create read-only roles for compliance reviewers
High-Volume Automation Teams
High-Volume Automation Teams
Scenario: Your automation specialists need guaranteed compute capacity while general users have occasional needs.Solution:
- Allocate higher concurrent run limits (8-12) to dedicated automation specialists
- Ensure power users have guaranteed capacity for critical workflows
- Prevent resource contention during peak automation periods
- Set lower limits (2-3) for occasional users
Getting Started
Access Role Management
Review Default Group
Examine the default role permissions and adjust as needed for your organization’s baseline requirements
Create Specialized Groups
Build roles for different user groups in your organization based on their responsibilities and needs
Assign Users
Move users from the default role to appropriate specialized groups based on their job functions
For additional support with Custom User Roles, contact your Gumloop support team at support@gumloop.com or reach out in your dedicated Slack channel.

