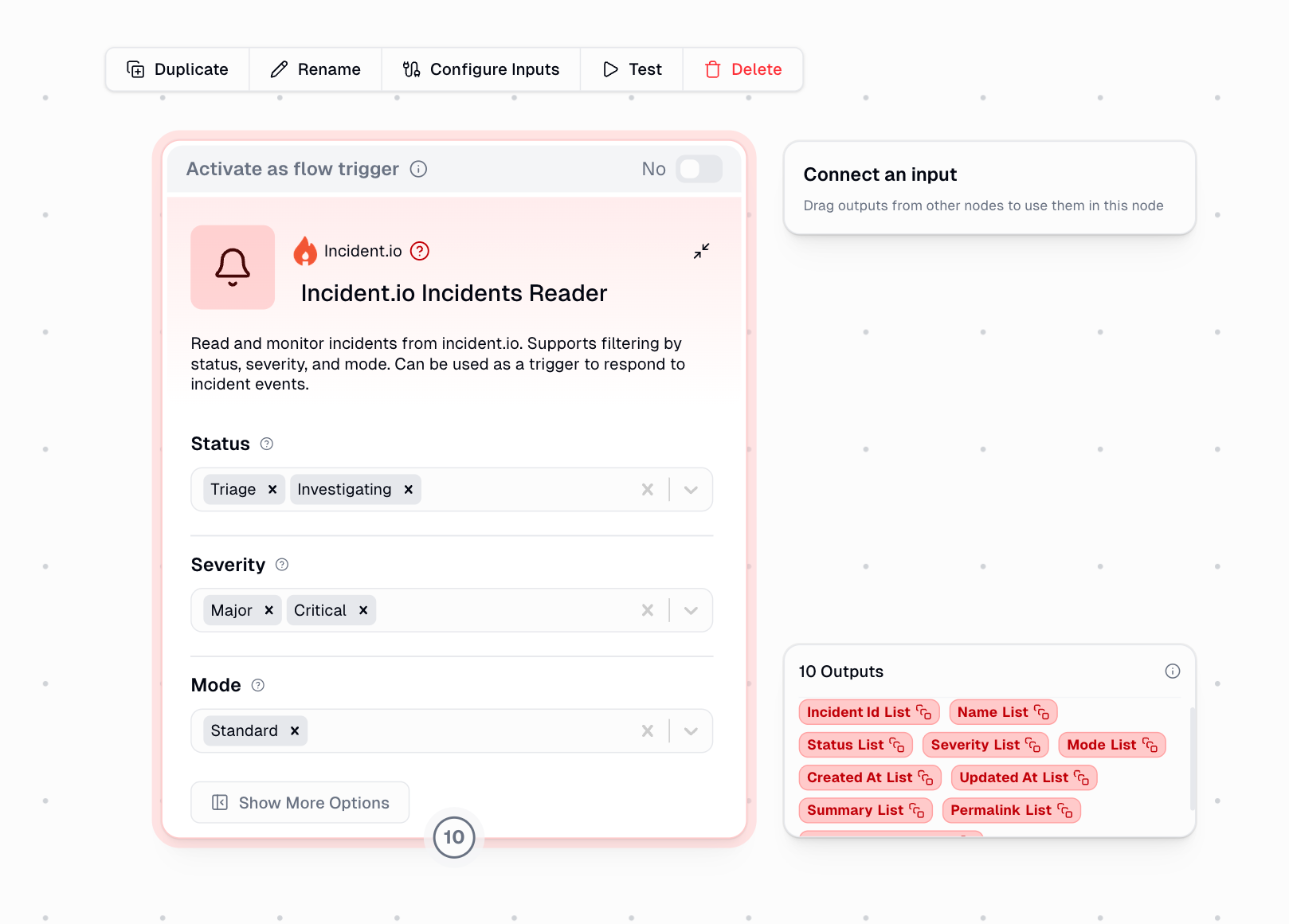
How It Works
This node operates in two modes:Manual Mode
Fetch incidents on-demand with custom filters. Returns all matching incidents as lists for reporting and analysis.
Trigger Mode
Automatically polls incident.io every 5 minutes for new incidents. Triggers your workflow when incidents are detected.
Setup
Get your API key
Navigate to your incident.io settings and generate an API key with permissions to read incidents.
Add the secret to Gumloop
Search for
Incident.io on the personal credentials page and save the API key.Configuration
Filters
All filters support multiple selections and use case-insensitive matching:Status
Status
Filter incidents by their current status:
- Triage - Incident is being assessed
- Investigating - Team is diagnosing the issue
- Fixing - Solution is being implemented
- Monitoring - Fix deployed, watching for stability
- Closed - Incident resolved
Severity
Severity
Filter by incident severity level:
- Minor - Low impact incidents
- Major - Significant business impact
- Critical - Severe, immediate attention required
Mode
Mode
Filter by incident type:
- Standard - Regular production incidents
- Retrospective - Post-incident analysis
- Tutorial - Training incidents
- Test - Testing workflows
Outputs
The node provides comprehensive incident data. Output format depends on the mode:| Output Field | Description | Source Field |
|---|---|---|
| Incident ID | Unique identifier | id |
| Name | Incident title | name |
| Status | Current status (Triage, Investigating, etc.) | incident_status.name |
| Severity | Severity level (Minor, Major, Critical) | severity.name |
| Mode | Incident type | mode |
| Created At | Creation timestamp (ISO format) | created_at |
| Updated At | Last update timestamp (ISO format) | updated_at |
| Summary | Incident description | summary |
| Permalink | Direct link to incident | permalink |
| Slack Channel ID | Associated Slack channel | slack_channel_id |
Manual mode returns arrays (lists) for each field. Trigger mode returns single values for each detected incident.
Using as a Trigger
When enabled as a trigger, the node automatically monitors for new incidents:- How Polling Works
- Deduplication
- Checks incident.io every 5 minutes
- Applies Severity and Mode filters (Status is not used in polling)
- Tracks processed incidents to avoid duplicates
- Fires workflow once per new incident detected
Common Trigger Use Cases
Slack Notifications
Automatically post to Slack when critical incidents are created
Ticket Creation
Create Jira or Linear tickets for new high-priority incidents
Team Alerts
Send email or SMS alerts when specific types of incidents occur
Incident Dashboard
Update real-time dashboards when incident status changes
Example Workflows
Daily Incident Report
Daily Incident Report
Run the node manually (no trigger) to fetch all incidents, filter by status (Investigating, Fixing), and pass the arrays to a reporting node. Perfect for daily standups or retrospectives.
Critical Incident Response
Critical Incident Response
Enable as a trigger with Severity set to Critical. Connect to nodes that post to Slack, create a PagerDuty alert, and log to your incident tracking system.
Incident Analysis Pipeline
Incident Analysis Pipeline
Fetch closed incidents weekly, extract patterns from summaries using AI, and generate insights about recurring issues.
Error Handling
The node provides clear error messages for common issues:| Error | Cause | Solution |
|---|---|---|
| No incidents found | incident.io returned zero incidents | Check your API permissions and ensure incidents exist |
| No incidents match filters | All incidents filtered out | Adjust your Status, Severity, or Mode filters |
| Failed to connect (HTTP error) | API request failed | Verify your API key and check incident.io service status |
| Empty response | API returned no data | Contact incident.io support if persistent |
| Invalid JSON | Response parsing failed | Check API compatibility or contact support |
In trigger mode, if no event is found in the webhook input, ensure the trigger is properly configured and the polling mechanism is active.

